Search This Blog
notes, ramblings, contemplations, transmutations, and otherwise ... on management and directory miscellanea.
Posts
Showing posts from 2012
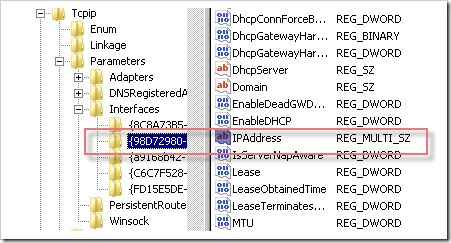
winnate - problems connecting to wireless networks
- Get link
- Other Apps
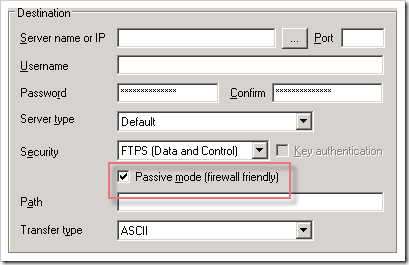
problem encountered using ftp-ssl with opalis (and corrected)
- Get link
- Other Apps
retrieving wmi class mof information
- Get link
- Other Apps
finding the right nic in server core
- Get link
- Other Apps
winnate – modifying hidden sizes
- Get link
- Other Apps
atlanta systems management user group [atlsmug] meeting 9/7/2012!
- Get link
- Other Apps
system center 2012 configuration manager ... UNLEASHED!
- Get link
- Other Apps
atlanta techstravaganza presentations
- Get link
- Other Apps
error when using add-type with microsoft.exchange.webservices.dll
- Get link
- Other Apps
enumerating dns records with powershell
- Get link
- Other Apps
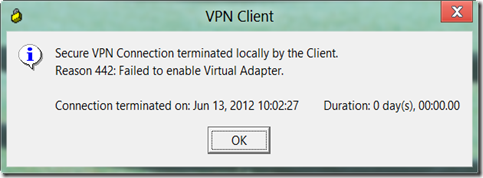
winnate – using windows 8 with cisco vpn
- Get link
- Other Apps
self-study guide for system center
- Get link
- Other Apps
checking dns forwarders of all domain controllers
- Get link
- Other Apps
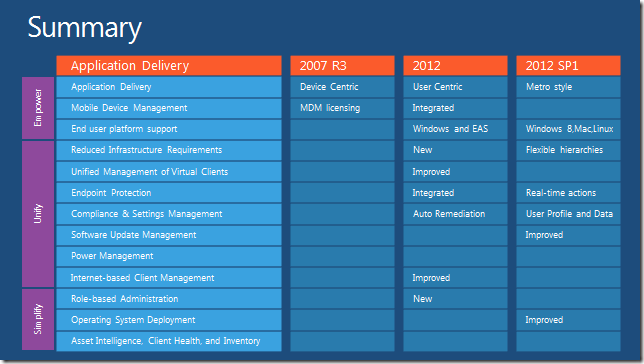
configuration manager 2012 service pack 1
- Get link
- Other Apps
opsmgr is running around crashing servers
- Get link
- Other Apps
self-study guide for system center endpoint protection
- Get link
- Other Apps
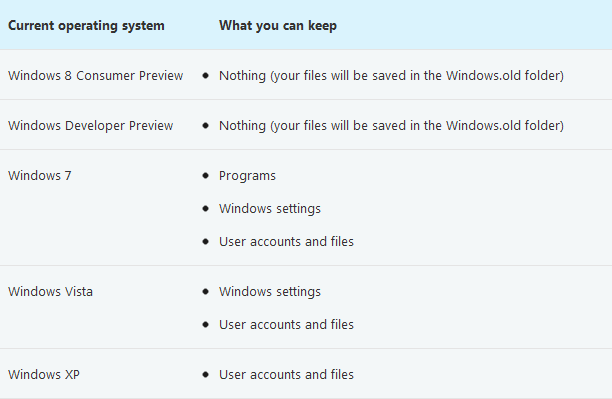
upgrading to windows 8 release preview
- Get link
- Other Apps
two upcoming events i wanted to mention
- Get link
- Other Apps
"get computer/ip status" activity throws raw socket error
- Get link
- Other Apps
managing client remediation in configmgr 2012
- Get link
- Other Apps
ntlm authentication is not dead nor are its problems
- Get link
- Other Apps