How to Identify Applications Using Your Domain Controller
Problem
Everyone has been through it. We've all had to retire or replace a domain controller at some point in our checkered collective experiences. While AD provides very intelligent high availability, some applications are just plain dumb.They do not observe site awareness or participate in locating a domain controller. All they want is the name or IP of one domain controller which gets hardcoded in a configuration file somewhere, deeply embedded in some file folder or setting that you are never going to find.
How do you look at a DC and decide which applications might be doing it? Packet trace? Logs? Shut it down and wait for screaming? It seems very tedious and nearly impossible.
Potential Solution
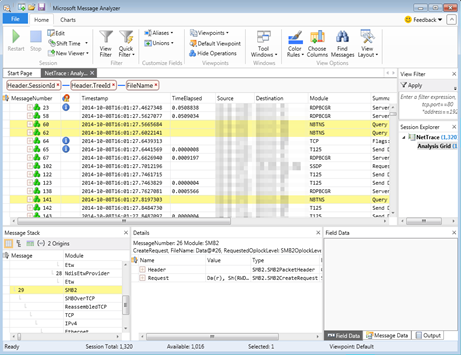
Obviously I wouldn't even bother posting this if I hadn't run across something interesting. :) I ran across something in draftcalled Domain Controller Isolation. Since it's in draft, I don't know that it's published yet. HOWEVER, the concept is based off these two posts:- https://blogs.technet.microsoft.com/pie/2014/07/13/how-to-detect-applications-using-hardcoded-dc-name-or-ip/
- https://blogs.technet.microsoft.com/askpfeplat/2013/12/15/domain-and-dc-migrations-how-to-monitor-ldap-kerberos-and-ntlm-traffic-to-your-domain-controllers/
- Using GPO, set the DC not to register its SRV records.
- Set up a custom monitor data collector to log these providers:
- Active Directory Domain Services: Core
- Active Directory: Kerberos KDC
- NTLM Security Protocol
- Convert the data to something human readable:
- tracerpt -l "mydata.etl" -of CSV
- Import it into the spreadsheet.
Maybe.
This comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDelete