Bind Response: InvalidCredentials
Sometimes I get the strangest things that come across my desk. As a manager, I don’t have a lot of time for troubleshooting so when I do get ahold of something, it’s fun to tear apart. I told my team about my findings. One of them asked how I arrived at the answer… so I thought I’d blog it just in case it interests anyone else.
As a favor to a coworker, I looked into an application configuration problem that was described as such:
- Application is configured for LDAP.
- All users can successfully log into the application except one person.
- This one person is also the administrator of the application.
The app owner indicated they were seeing timeout errors in their logs. There was no denying it. The call was timing out:
Servlet.service() for servlet dispatcher threw exception javax.naming.NamingException: LDAP response read timed out, timeout used:-1ms.; remaining name '' at com.sun.jndi.ldap.Connection.readReply(Connection.java:483) at com.sun.jndi.ldap.LdapClient.getSearchReply(LdapClient.java:639) at com.sun.jndi.ldap.LdapClient.search(LdapClient.java:562) at com.sun.jndi.ldap.LdapCtx.doSearch(LdapCtx.java:1985) at com.sun.jndi.ldap.LdapCtx.searchAux(LdapCtx.java:1847) at com.sun.jndi.ldap.LdapCtx.c_search(LdapCtx.java:1772)
To respond to that, the first thing we did was check the LDAP configuration to make sure it wasn’t misconfigured anywhere. I couldn’t tell if they what it was timing out to. A bind request? A search request? Who knows.
What little there was in the ldap.properties file looked appropriately set so they went back to scour more logs. I asked them to verify there was no application wonkiness by making someone else an admin and having them log on. Negative. All good. Now we’re getting somewhere.
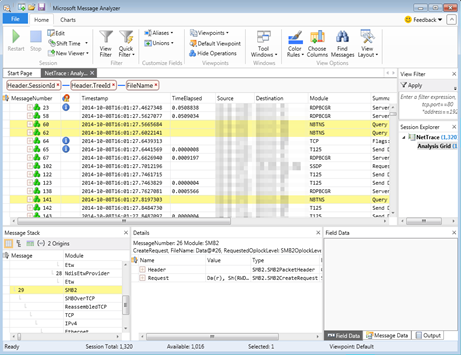
Of course, you never find the log that tells you exactly what’s going on. I’m pretty sure this is why packet tracing became a thing. I asked for a trace. This is what the trace revealed:
Now we can confirm that indeed the user’s attempt to bind fails. He had no problem logging into other things though -- his workstation for example. I told the app team that the user was not providing his credentials properly, or it was an application problem. They weren’t sure where to go next. I figured it had to be the logon form, though, so I tried one more thing.
I asked the user to tell me the character length of his password and verified the character length of the form. The form truncated at least two characters off his password. The password is masked and at such a length that you might not realize little dots weren’t continuing to show up. :o)
PROBLEM SOLVED! The LDAP response InvalidCredentials was indeed correct. Once you get the application logs out of the way and go straight down to the packet, you can see so much more. That’s my lesson of the day.


Comments
Post a Comment