Search This Blog
notes, ramblings, contemplations, transmutations, and otherwise ... on management and directory miscellanea.
Posts
Showing posts from April, 2008
another blog to add to your long list of news feeds...
- Get link
- X
- Other Apps
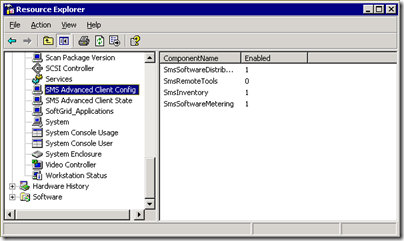
inventory sms advanced client component configuration...
- Get link
- X
- Other Apps
how to retrieve your ip address with powershell...
- Get link
- X
- Other Apps